Dictionary attacks
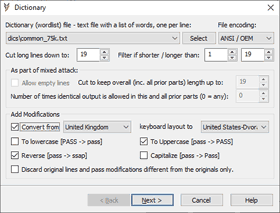
Dictionary (D) attack is a basic password recovery attack. Password candidates are generated based on a list (wordlist) loaded from a file. It can be a list of common passwords, names, nicknames, national capitals, action figures, words from any language, etc. Several wordlists are already included with our tools and personalized wordlist can be created as a plain text file with one password candidate per line and selected with "Select" button. Common encodings are supported and detected automatically, but can be set manually as well. Lines are cut down to a maximum password size allowed by default. Additional length-based filtering is available. For example, you can set the filter as N-N to load N chars long lines only or set cut down to N as well, to cut all longer lines down to N chars to pass filtering. Empty lines are filtered by default and "Allow empty lines" option allows you to pass empty lines in mixed attack setup as a valid output to be joined with other parts. "Cut to keep overall length no longer than N" is also available for mixed attack setup. It is set to a maximum password length allowed by default and thus ignored, but can be employed to pad previous parts up to a fixed length using dictionary attack output. "Number of times identical output is allowed..." can be used to combine several wordlists in mixed attack and exclude undesirable repetitions. Keyboard layouts conversion is available for systems with 2 or more keyboard layouts installed. Several other modifications are offered to transform every line from the list (such as reverse and case variations). For example, word "pass" with 'reverse' and 'to uppercase' options enabled will transform into the following 4 variants: "pass", "ssap", "PASS", "SSAP" Modified forms are verified after the source line from a wordlist. "Discard original lines..." option allows you to verify modified variants only, thus additional modifications can be used without retesting the source.
All trademarks are the property of their respective holders.