Mixed attacks are designed to search for passwords with known parts or patterns that can be spitted into parts (e.g. known part + unknown part, dictionary word + year, name + zip code, etc.).
Parts are joined into password candidate to be verified. Password = "Part1"+"Part2"+"Part3"+... = "Part1Part2Part3...".
The easiest way to imagine it is a digital clock (hours, minutes and seconds as parts) with 24*60*60=86400 combinations from 00:00:00 to 23:59:59.
Main building blocks are fixed (known), brute-force and dictionary parts.
Mixed attack can also be extended with:
simple modifications - add part(s) copy or reverse copy, substitute chars.
multi-position move - move part within chars from previous parts.
multi-position mutations - typing errors, char replacements, case switching.
Parts and attack outputs are displayed during setup to simplify configuration and verification. You may also check step-by-step mixed attack example.
Example 1:
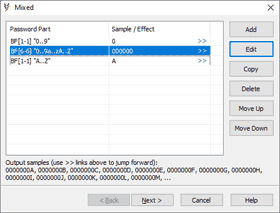
Let's say there is no information about the password except for "0..9A..Za..z" charset and the fact that the first char is a digit and the last one is an uppercase letter. Let’s say the password length is 8 chars.
Brute-force attack for 8 chars with "0..9A..Za..z" charset includes 62^8 (68 to the power of 8) passwords.
3 parts mixed attack:
<digit> - brute-force, 1 char, "0..9" charset.
<unknown> - brute-force, 6 chars, "0..9A..Za..z" charset.
<uppercase letter> - brute-force, 1 char, "A..Z" charset.
This mixed attack includes 10 * 62^6 * 26 passwords and it is just 7% from the full brute-force.
Multi-position mods can be used to try <digit> and <uppercase letter> parts in different positions.
Example 1 + multi-computer processing:
Mixed attacks can also be used to split the search between several PCs. Here is how the first part can be used to split workload for the example above:
PC1: <digit> - brute-force, 1char, "0..4" charset.
PC2: <digit> - brute-force, 1char, "5..9" charset.
Example 2:
Let's say company documents are protected with passwords:
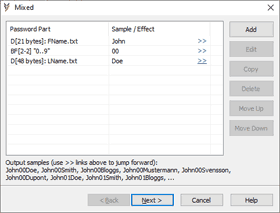
"<FName><Year><LName>"
(e.g. "John14Smith" or "Fred98Bloggs")
Parts are as following:
<FName> – dictionary: first name.
<Year> – brute-force, 2 chars, "0..9" charset.
<LName> – dictionary: last name.
Example 3:
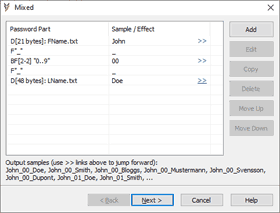
How about Example 2 passwords but with parts divided by underscore:
"<FName>_<Year>_<LName>"
(e.g. "John_14_Smith" or "Fred_98_Bloggs")
Now there are 5 parts:
<FName> - dictionary: first name
Fixed "_"
<Year> - brute-force, 2 chars, "0..9" charset.
Fixed "_"
<LName> - dictionary: last name