DMG Password Recovery
DMG Password by Thegrideon Software is a feature-rich and highly-optimized password recovery tool for OS X and macOS Disk Image files ('.dmg', '.sparseimage'). Both 128 and 256 bit AES encryption methods are supported. DMG Password is designed for MS Windows. Please use trial version to test compatibility layers and virtual machines on other platforms.
DMG Password Recovery Features:
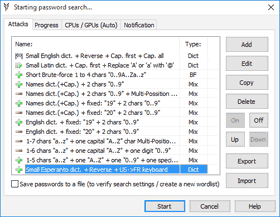
- Several password search attacks can be configured and queued:

- advanced mixed attacks for precise search range setup:
- multi-position moves to cover modern password policies;
- simple modifications: add part(s) copy, replace chars, etc.
- typing errors, case switching, char substitutions;
- brute-force attacks based on a charset and length selected:
- limit number of equal, capital or special chars or digits;
- dictionary attacks with modifications (several wordlists are included):
- advanced keyboard layouts-aware recovery technique;
- password in reverse, capitalized, uppercased, lowercased;
- number ranges (e.g. 1-31, 01-12, 2013-2020, etc.);
- "Output attacks to a file" option to verify search settings, generate new wordlist, etc.
- Audio, script or web address based post-search notification.
- Highly optimized code (SSE, AVX, AVX2, AVX-512) guarantees best performance.

- Utilizes NVIDIA and AMD Graphics processing units with a high-performance methods.
- Supports up to 64 simultaneous processing threads (multi-CPU, multi-GPU).
- Windows 7 - Windows 11.
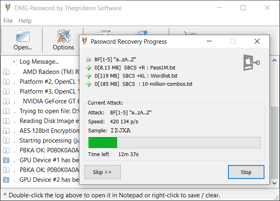
.dmg and .sparseimage disk image files password protection is based on PBKDF2 key derivation function and AES-128 or AES-256 encryption algorithms. Passwords are hashed with thousands of iterations, thus recovery speed is limited, but we did our best to enhance this tool performance (recovery speed) with some advanced methods. DMG Password allows you to setup a very precise search range to exploit known password details (parts and patterns) and reduce the search time required in comparison to traditional attacks. Just check mixed attacks for example.You may also check Password Search FAQ.
Disk Image encryption complexity (number of hash iterations) is variable from file to file (from 1000 upto 300 000). The following tables are based on .dmg files with 100 000 iterations.
The final password recovery speed is equal to CPUspeed + GPU(1)speed + ... + GPU(N)speed.
For example: Intel Core i3 + AMD R9 270 = 250 + 3500 = ~3750 p/s.
| CPU: |
|---|
| Instructions Set: |
| Speed p/s: |
| Intel® Core™2 Duo T7500 @ 2.20GHz |
Intel® Core™ i3 2100 @ 3.10GHz |
Intel® Core™ i3 4130 @ 3.40GHz |
Amazon EC2 "c5.large" Xeon® Platinum core |
|---|---|---|---|
| SSE2 | AVX | AVX2 | AVX512 |
| ~50 | ~110 | ~250 | ~300 |
AMD and Nvidia GPUs
Compute units or stream multiprocessors (CU, SM, SMX, SMM) are the main building blocks of GPU calculation power, thus 32xCU GPU card is usually twice as fast as 16xCU GPU card of the same family and architecture running at the same frequency.
You can expect approximately 300-400 p/s performance per every Nvidia SM running at 1Ghz and approximately 150-200 p/s per every AMD CU.
| GT 640 (Kepler) 2xSMX, 1045 MHz |
Tesla M60 (Maxwell) 16xSMx, 1150 MHz |
GTX 1080 Ti (Pascal) 28xSM, 1580 Mhz |
Tesla V100 (Volta) 80xSM, 1380 Mhz |
|---|---|---|---|
| + 670 p/s | + 7 700 p/s | + 22 000 p/s | + 33 000 p/s |
| 670/2/1.05=319 | 7700/16/1.15=418 | 22000/28/1.58=500 | 33000/80/1.38=300 |
| HD 6770 (VLIW5) 10xCU, 850 Mhz |
R9 270 (GCN 1) 20xCU, 950 MHz |
RX 480 (GCN 4) 36xCU, 1260 MHz |
RX Vega 64 (GCN 5) 64xCU, 1500 MHz |
|---|---|---|---|
| + 1 750 p/s | + 3 500 p/s | + 7 900 p/s | + 17 000 p/s |
| 1750/10/0.85=205 | 3500/20/0.95=185 | 7900/36/1.26=175 | 17000/64/1.50=180 |
It is important to mention that AMD and NVIDIA architectures are quite different and although AMD per CU performance is lower, there are more CUs per card in a similar price range. Moreover GPU performance is somewhat variable with number of factors including GPU/CPU combination and even a driver version. Please contact us if your recovery speed is noticeable different from the data above.
Trial version is available to check format and hardware compatibility. It allows you to setup and test run any password search for up to 15 min per run. Recovered passwords are hidden behind the asterisks.
All trademarks are the property of their respective holders.