Word Password Recovery
Word Password by Thegrideon Software is an advanced and highly-optimized password recovery tool for MS Word Documents and Templates (*.docx, *.dotx, *.doc, *.dot, ...). It supports MS Word 2007 - 2021 & Office 365 files (new XML-based formats) as well as MS Word 97 - 2003 files (old binary formats). You may also check VBA Recovery Toolkit to handle locked VBA Projects.
Word Password Recovery Features:
- All Word 97-2024 / Office 365 encryption methods are supported.
- Write Protection passwords can be recovered or removed instantly.
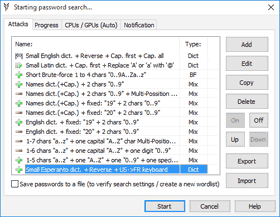
- Several "password to open" search attacks can be configured and queued:

- advanced mixed attacks for precise search range setup:
- multi-position moves to cover modern password policies;
- simple modifications: add part(s) copy, replace chars, etc.
- typing errors, case switching, char substitutions;
- brute-force attacks based on a charset and length selected:
- limit number of equal, capital or special chars or digits;
- dictionary attacks with modifications (several wordlists are included):
- advanced keyboard layouts-aware recovery technique;
- password in reverse, capitalized, uppercased, lowercased;
- number ranges (e.g. 1-31, 01-12, 2013-2020, etc.);
- "Output attacks to a file" option to verify search settings or to generate a new wordlist, etc.
- Highly optimized code (SSE, AVX, AVX2, AVX-512) guarantees best performance.

- Utilizes NVIDIA and AMD Graphics processing units with a high-performance methods.
- Utilizes modern Intel integrated GPUs.

- Supports up to 64 simultaneous processing threads (multi-CPU, multi-GPU).
- Audio, script or web address based post-search notification.
- Windows 7 - Windows 11.
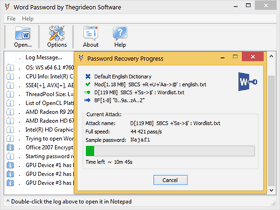
Encryption methods used in Word 97 - 2003 are not very strong by today standards and there is a way to remove file protection with guarantee (please check WordDecryptor), however there is no way to recover original password without password search and if the password is as important as document content than Word Password allows you to search through millions of passwords per second. Methods used in "password to open" protection in Word 2007 - 2024 are based on strong encryption algorithms (SHA-1, SHA-512, AES) and instant password recovery or decryption cannot be guaranteed in contrast to prior MS Word versions. Moreover recovery speed is limited due to iterative methods used in password verification. In order to recover these types of passwords, candidates have to be created based on dictionary, sequentially based on a charset and length selected or created as a combination of dictionary, sequential and fixed parts. Word Password allows you to set several attacks in a queue for precise search range setup, split password pattern in parts and set each part independently with virtually endless number of combinations. Additional modifications are available including unique keyboard layouts-aware recovery technique, char replacement (e.g. I or i with 1), etc.You may also check Password Search FAQ.
We did our best to enhance this tool performance as well as the recovery speed with some advanced methods and it found to be the fastest tool for MS Word "password to open" recovery. Password recovery speed for a very common hardware is available below to back this statement up.
Word 97 - 2003:
| CPU only: |
|---|
| 40bit RC4: |
| CryptoAPI: |
| Intel® Core™2 Duo T7500 @ 2.20GHz |
Intel® Atom™ Z3740 @ 1.33GHz |
Intel® Core™ i3 2100 @ 3.10GHz |
Intel® Core™ i3 4130 @ 3.40GHz |
|---|---|---|---|
| 1 550 000 p/s | 1 900 000 p/s | 3 700 000 p/s | 4 600 000 p/s |
| 1 350 000 p/s | 1 600 000 p/s | 3 200 000 p/s | 4 100 000 p/s |
Word 2007 - 2024:
The final password recovery speed is equal to CPUspeed + GPU(1)speed + ... + GPU(N)speed.
For example (Word 2007): Intel i3 + integrated HD 4400 GPU + AMD R9 270 = 2 100 + 820 + 27 300 = ~30 000 p/s (passwords per second).
| CPU: |
|---|
| Instructions Set: |
| Word 2007: |
| Word 2010: |
| 2013 - 2024: |
| Intel® Core™2 Duo T7500 @ 2.20GHz |
Intel® Core™ i3 2100 @ 3.10GHz |
Intel® Core™ i3 4130 @ 3.40GHz |
Amazon EC2 "c5.large" Xeon® Platinum core |
|---|---|---|---|
| SSE2 | AVX | AVX2 | AVX512 |
| ~470 p/s | ~940 p/s | ~2 100 p/s | ~2 500 p/s |
| ~230 p/s | ~475 p/s | ~1 050 p/s | ~1 200 p/s |
| ~30 p/s | ~60 p/s | ~135 p/s | ~210 p/s |
Integrated GPUs
Modern integrated GPUs (like Intel HD and Iris Graphics) can be used for password recovery acceleration. Integrated GPUs are not as powerful as dedicated (discrete) devices and often overlooked but can add up to 30% to CPU performance.
AMD and Nvidia GPUs
Compute units or stream multiprocessors (CU, SM, SMX, SMM) are the main building blocks of GPU calculation power, thus 32xCU GPU card is usually twice as fast as 16xCU GPU card of the same family and architecture running at the same frequency.
The table below shows expected performance per SM / CU for Nvidia and AMD GPUs as well as several actual examples.
| NVIDIA GPU: |
|---|
| Per SM at 1000 MHz |
| Tesla K80 (Kepler 2.0) 2x13xSMX, 820 MHz |
| Tesla V100 (Volta) 80xSM, 1380 Mhz |
| Word 2007: | Word 2010: | 2013 - 2024: |
|---|---|---|
| 2000-3000 p/s | 1000-1500 p/s | 150-200 p/s |
| 54 000 p/s 54000/26/0.82=2500 |
27 000 p/s 27000/26/0.82=1250 |
3 300 p/s 3300/26/0.82=155 |
| 240 000 p/s 240000/80/1.38=2175 |
120 000 p/s 120000/80/1.38=1090 |
18 000 p/s 18000/80/1.38=160 |
| AMD GPU: |
|---|
| Per CU at 1000MHz |
| R9 270 (GCN 1.0) 20xCU, 950 MHz |
| RX 480 (GCN 4.0) 36xCU, 1250 MHz |
| Word 2007: | Word 2010: | 2013 - 2024: |
|---|---|---|
| 1300-1600 p/s | 700-750 p/s | 100-150 p/s |
| 27 000 p/s 27000/20/0.95=1400 |
13 800 p/s 13800/20/0.95=725 |
2 400 p/s 2400/20/0.95=125 |
| 60 500 p/s 60500/36/1.25=1350 |
30 900 p/s 30900/36/1.25=690 |
5 100 p/s 5100/36/1.25=115 |
It is important to mention that AMD and NVIDIA architectures are quite different and although AMD per CU performance is lower, there are more CUs per card in a similar price range. Moreover GPU performance is somewhat variable with number of factors including GPU/CPU combination and even a driver version. Please contact us if your recovery speed is noticeably different from the data above.
Trial version can be used to check format and hardware compatibility. It allows you to setup and test run any password search for up to 15 min per set. Recovered passwords are hidden behind the asterisks.
All trademarks are the property of their respective holders.